What's new arround internet
| Src | Date (GMT) | Titre | Description | Tags | Stories | Notes |
| 2017-02-15 09:56:45 | (Déjà vu) Russian Cyberspies Use New Mac Malware to Steal Data (lien direct) | Researchers have discovered a new piece of malware used by the Russia-linked threat group known as APT28 to steal sensitive data from Mac devices, including backups and passwords. | APT 28 | |||
| 2017-02-15 07:35:38 | Mac Malware Linked to Infamous Russian Cyber-Espionage Group (lien direct) | Russian cyberspies known as APT28 have created a Mac version of their famous XAgent (X-Agent, Sofacy) malware, which already has versions for Windows, iOS, and Android. [...] | APT 28 | |||
| 2017-02-14 10:09:15 | Russian cyberspies blamed for US election hacks are now targeting Macs (lien direct) | Security researchers have discovered a macOS malware program that's likely part of the arsenal used by the Russian cyberespionage group blamed for hacking into the U.S. Democratic National Committee last year.The group, which is known in the security industry under different names, including Fancy Bear, Pawn Storm, and APT28, has been operating for almost a decade. It is believed to be the sole user and likely developer of a Trojan program called Sofacy or X-Agent.X-Agent variants for Windows, Linux, Android, and iOS have been found in the wild in the past, but researchers from Bitdefender have now come across what appears to be the first macOS version of the Trojan.To read this article in full or to leave a comment, please click here | APT 28 | |||
| 2017-02-13 16:53:47 | Fancy Bear: who\'s behind the group implicated in so many political hacks? (lien direct) | What do we know about the group known as Fancy Bear? Geoff White of Channel 4 News sifts through the evidence about the hacking group behind some high-profile cyber-attacks |
APT 28 | |||
| 2017-02-13 16:52:34 | DHS Uses Cyber Kill Chain to Analyze Russia-Linked Election Hacks (lien direct) | DHS Publishes Enhanced Analysis Report on GRIZZLY STEPPE Activity | APT 29 APT 28 | |||
| 2017-01-27 17:55:54 | News in brief: Fancy Bear \'attacked TV network\'; Lavabit comes back to life; museum does geek history (lien direct) | Your daily round-up of some of the other stories in the news |
APT 28 | |||
| 2017-01-27 13:00:41 | Sednit: How this notorious cyberespionage group operates (lien direct) | Take a closer look at the cyberespionage group Sednit, which has targeted over 1000 high-profile individuals and organizations with phishing attacks and zero-day exploits. | APT 28 | |||
| 2017-01-11 04:00:46 | 10 Questions that Need to Be Asked about Every Cybersecurity Story (lien direct) | The Russian hacking fiasco we’ve been following over the past weeks – hysteria, which is due to the flawed Grizzly Steppe report and subsequent haphazard news reporting – has done a grave disservice to the serious issue of national cybersecurity. If the world is going to ever turn the corner from its current state of […]… Read More | APT 29 APT 28 | |||
| 2017-01-04 17:40:00 | DHS-FBI Report Shows Russian Attribution\'s A Bear (lien direct) | Political and technical fallout from the DHS-FBI joint 'Grizzly Steppe' report on Russia's role in the recent election-related hacks causes more chaos than closure. | APT 29 APT 28 | |||
| 2017-01-03 21:33:01 | Dear Obama, From Infosec (lien direct) | Dear President Obama:We are more than willing to believe Russia was responsible for the hacked emails/records that influenced our election. We believe Russian hackers were involved. Even if these hackers weren't under the direct command of Putin, we know he could put a stop to such hacking if he chose. It's like harassment of journalists and diplomats. Putin encourages a culture of thuggery that attacks opposition, without his personal direction, but with his tacit approval.Your lame attempts to convince us of what we already agree with has irretrievably damaged your message.Instead of communicating with the America people, you worked through your typical system of propaganda, such as stories in the New York Times quoting unnamed "senior government officials". We don't want "unnamed" officials -- we want named officials (namely you) who we can pin down and question. When you work through this system of official leaks, we believe you have something to hide, that the evidence won't stand on its own.We still don't believe the CIA's conclusions because we don't know, precisely, what those conclusions are. Are they derived purely from companies like FireEye and CloudStrike based on digital forensics? Or do you have spies in Russian hacker communities that give better information? This is such an important issue that it's worth degrading sources of information in order to tell us, the American public, the truth.You had the DHS and US-CERT issue the "GRIZZLY-STEPPE" report "attributing those compromises to Russian malicious cyber activity". It does nothing of the sort. It's full of garbage. It contains signatures of viruses that are publicly available, used by hackers around the world, not just Russia. It contains a long list of IP addresses from perfectly normal services, like Tor, Google, Dropbox, Yahoo, and so forth.Yes, hackers use Yahoo for phishing and malvertising. It doesn't mean every access of Yahoo is an "Indicator of Compromise".For example, I checked my web browser [chrome://net-internals/#dns] and found that last year on November 20th, it accessed two IP addresses that are on the Grizzley-Steppe list: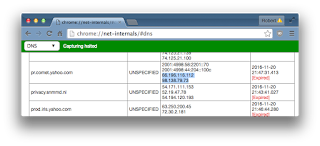 No, this doesn't mean I've been hacked. It means I just had a normal interaction with Yahoo. It means the Grizzley-Steppe IoCs are garbage.If your intent was to show technical information to experts to confirm Russia's involvement, you've done the precise opposite. Grizzley-Steppe proves such enormous incompetence that we doubt all the technical details you might have. I mean, it's possible that you classified the important details and de-classified the junk, but even then, that junk isn't worth publishing. There's no excuse for those Yahoo addresses to be in there, or the numerous other problems.Among the consequences is that Washington Post story claiming Russians hacked into the Vermont power grid. What really happened is that somebody just checked their Yahoo email, thereby accessing one of the same IP addresses I did. How they get from the facts (one person accessed Yahoo email) to the story (Russians hacked power grid) is your responsibility. This misinformation is your fault.You announced sanctions for the Russian hacking [*]. At the same time, you announced sanctions for Russian harassment of diplomati No, this doesn't mean I've been hacked. It means I just had a normal interaction with Yahoo. It means the Grizzley-Steppe IoCs are garbage.If your intent was to show technical information to experts to confirm Russia's involvement, you've done the precise opposite. Grizzley-Steppe proves such enormous incompetence that we doubt all the technical details you might have. I mean, it's possible that you classified the important details and de-classified the junk, but even then, that junk isn't worth publishing. There's no excuse for those Yahoo addresses to be in there, or the numerous other problems.Among the consequences is that Washington Post story claiming Russians hacked into the Vermont power grid. What really happened is that somebody just checked their Yahoo email, thereby accessing one of the same IP addresses I did. How they get from the facts (one person accessed Yahoo email) to the story (Russians hacked power grid) is your responsibility. This misinformation is your fault.You announced sanctions for the Russian hacking [*]. At the same time, you announced sanctions for Russian harassment of diplomati |
Yahoo APT 29 APT 28 | |||
| 2017-01-02 16:29:22 | U.S. Gov\'s "GRIZZLY STEPPE" Report Fails to Achieve Purpose: Experts (lien direct) | The recently released Joint Analysis Report (JAR) published by the Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI) to detail tools used by Russian hackers in cyber attacks against the United States election didn't deliver on its promise, security experts argue. | APT 29 APT 28 | |||
| 2016-12-30 19:30:10 | FBI-DHS Report Links Fancy Bear Gang to Election Hacks (lien direct) | Joint report “Grizzly Steppe†implicates Russian hacking group Fancy Bear in U.S. election-related hacking. | APT 29 APT 28 | |||
| 2016-12-29 20:40:33 | Some notes on IoCs (lien direct) | Obama "sanctioned" Russia today for those DNC/election hacks, kicking out 35 diplomats, closing diplomatic compounds, seizing assets of named individuals/groups. They also published "IoCs" of those attacks, fingerprints/signatures that point back to the attackers, like virus patterns, file hashes, and IP addresses.These IoCs are of low quality. They are published as a political tool, to prove they have evidence pointing to Russia. They have limited utility to defenders, or those publicly analyzing attacks.Consider the Yara rule included in US-CERT's "GRIZZLY STEPPE" announcement: What is this? What does this mean? What do I do with this information?It's a YARA rule. YARA is a tool ostensibly for malware researchers, to quickly classify files. It's not really an anti-virus product designed to prevent or detect an intrusion/infection, but to analyze an intrusion/infection afterward -- such as attributing the attack. Signatures like this will identify a well-known file found on infected/hacked systems.What this YARA rule detects is, as the name suggests, the "PAS TOOL WEB KIT", a web shell tool that's popular among Russia/Ukraine hackers. If you google "PAS TOOL PHP WEB KIT", the second result points to the tool in question. You can download a copy here [*], or you can view it on GitHub here [*].Once a hacker gets comfortable with a tool, they tend to keep using it. That implies the YARA rule is useful at tracking the activity of that hacker, to see which other attacks they've been involved in, since it will find the same web shell on all the victims.The problem is that this P.A.S. web shell is popular, used by hundreds if not thousands of hackers, mostly associated with Russia, but also throughout the rest of the world (judging by hacker forum posts). This makes using the YARA signature for attribution problematic: just because you found P.A.S. in two different places doesn't mean it's the same hacker.A web shell, by the way, is one of the most common things hackers use once they've broken into a server. It allows further hacking and exfiltration traffic to appear as normal web requests. It typically consists of a script file (PHP, ASP, PERL, etc.) that forwards commands to the local system. There are hundreds of popular web shells in use.We have little visibility into how the government used these IoCs. IP addresses and YARA rules like this are weak, insufficient for attribution by themselves. On the other hand, if they've got web server logs from multiple victims where commands from those IP addresses went to this specific web shell, then the attribution would be strong that all these attacks are by the same actor.In other words, these rules can be a reflection of the fact the government has excellent information for attribution. Or, it could be a reflection that they've got only weak bits and pieces. It's impossible for us outsiders to tell. IoCs/signatures are fetishized in the cybersecurity community: they love the small rule, but they ignore the complexity and context around the rules, often misunderstanding what's going on. (I've written thousands of the things -- I'm constantly annoyed by the ignorance among those not understanding what they mean).I see on What is this? What does this mean? What do I do with this information?It's a YARA rule. YARA is a tool ostensibly for malware researchers, to quickly classify files. It's not really an anti-virus product designed to prevent or detect an intrusion/infection, but to analyze an intrusion/infection afterward -- such as attributing the attack. Signatures like this will identify a well-known file found on infected/hacked systems.What this YARA rule detects is, as the name suggests, the "PAS TOOL WEB KIT", a web shell tool that's popular among Russia/Ukraine hackers. If you google "PAS TOOL PHP WEB KIT", the second result points to the tool in question. You can download a copy here [*], or you can view it on GitHub here [*].Once a hacker gets comfortable with a tool, they tend to keep using it. That implies the YARA rule is useful at tracking the activity of that hacker, to see which other attacks they've been involved in, since it will find the same web shell on all the victims.The problem is that this P.A.S. web shell is popular, used by hundreds if not thousands of hackers, mostly associated with Russia, but also throughout the rest of the world (judging by hacker forum posts). This makes using the YARA signature for attribution problematic: just because you found P.A.S. in two different places doesn't mean it's the same hacker.A web shell, by the way, is one of the most common things hackers use once they've broken into a server. It allows further hacking and exfiltration traffic to appear as normal web requests. It typically consists of a script file (PHP, ASP, PERL, etc.) that forwards commands to the local system. There are hundreds of popular web shells in use.We have little visibility into how the government used these IoCs. IP addresses and YARA rules like this are weak, insufficient for attribution by themselves. On the other hand, if they've got web server logs from multiple victims where commands from those IP addresses went to this specific web shell, then the attribution would be strong that all these attacks are by the same actor.In other words, these rules can be a reflection of the fact the government has excellent information for attribution. Or, it could be a reflection that they've got only weak bits and pieces. It's impossible for us outsiders to tell. IoCs/signatures are fetishized in the cybersecurity community: they love the small rule, but they ignore the complexity and context around the rules, often misunderstanding what's going on. (I've written thousands of the things -- I'm constantly annoyed by the ignorance among those not understanding what they mean).I see on |
APT 29 APT 28 | |||
| 2016-12-29 17:00:00 | FBI, DHS Report Implicates Cozy Bear, Fancy Bear In Election-Related Hacks (lien direct) | US government dubs the operation "GRIZZLY STEPPE" in new Joint Analysis Report, and says the malicious groups' activity continues. | APT 29 APT 28 | |||
| 2016-12-22 17:57:31 | Fancy Bear used Android malware to track Ukrainian artillery (lien direct) |  Security researchers claim that a malicious Android app helped Russian forces deal heavy blows in Ukrainian crisis.
David Bisson reports. Security researchers claim that a malicious Android app helped Russian forces deal heavy blows in Ukrainian crisis.
David Bisson reports.
|
APT 28 | |||
| 2016-12-22 12:35:40 | Russia Used Android Malware to Track Ukrainian Troops: Report (lien direct) | The Russia-linked cyberespionage group known as Fancy Bear has tracked Ukrainian artillery forces by planting a piece of Android malware in a legitimate military application, threat intelligence firm CrowdStrike reported on Thursday. | APT 28 | |||
| 2016-12-22 12:15:00 | Malware Used In DNC Breach Found Tracking Ukraine Military (lien direct) | Russian 'Fancy Bear' now tied to Ukraine artillery Android app hack with the same malware used in breach of the Democratic National Committee. | APT 28 | |||
| 2016-12-22 11:51:45 | The group that hacked the DNC infiltrated Ukrainian artillery units (lien direct) | The cyberespionage group blamed for hacking into the U.S. Democratic National Committee (DNC) earlier this year has also infiltrated the Ukrainian military through a trojanized Android application used by its artillery units.The group, which is known in the security industry under different names, including Fancy Bear, Pawn Storm, and APT28, has been operating for almost a decade. It is believed to be the sole user and likely developer of a Trojan program called Sofacy or X-Agent that has variants for Windows, Android, and iOS.Fancy Bear has been responsible for many cyberespionage operations around the world over the years, and its selection of targets has frequently reflected Russia's geopolitical interests. Researchers from security firm CrowdStrike believe the group is likely tied to the Russian Military Intelligence Service (GRU).To read this article in full or to leave a comment, please click here | APT 28 | |||
| 2016-12-15 13:00:05 | Let It Ride: The Sofacy Group\'s DealersChoice Attacks Continue (lien direct) | Recently, Palo Alto Networks Unit 42 reported on a new exploitation platform that we called “DealersChoice†in use by the Sofacy group (AKA APT28, Fancy Bear, STRONTIUM, Pawn Storm, Sednit).  As outlined in our original posting, the DealersChoice exploitation platform generates malicious RTF documents which in turn use embedded OLE Word documents. These embedded OLE Word documents then contain embedded Adobe Flash (.SWF) files that are designed to exploit Abode Flash vulnerabilities. At the time of initial reporting, we found two variants: Variant A: A standalone variant that included Flash … | APT 28 | |||
| 2016-12-09 16:45:25 | Fancy Bear ramping up infowar against Germany-and rest of West (lien direct) | Russian hackers part of broader campaign against West, German intel chief warns. | APT 28 | |||
| 2016-12-09 16:17:42 | Germany Accuses Russia of Hybrid Warfare (lien direct) | Russia has been accused of waging its own brand of cyber hybrid warfare against Germany, with specific focus on next year's elections. In particular, the APT28 (Fancy Bear) hacking group -- thought to be linked to the Russian government -- is accused of spreading propaganda and disinformation under the guise of 'hacktivists'. | APT 28 | |||
| 2016-12-08 11:35:57 | Russian cyberspies likely behind DNC breach move on to German election (lien direct) | A group of suspected Russian cyberspies blamed for interfering in the U.S. election is also attempting to influence the upcoming vote in Germany, according to the country's domestic intelligence agency.The Russian hacking group known as Fancy Bear or APT 28 has been targeting political parties in the country, Germany's Federal Office for the Protection of the Constitution (BfV) intelligence agency said in a statement Thursday posted online by Politico.The hacking activities have led to a surge in spear-phishing email attacks directed at German politicians, the agency said.  To read this article in full or to leave a comment, please click here | APT 28 | |||
| 2016-12-02 09:52:54 | One Bit To Rule A System: Analyzing CVE-2016-7255 Exploit In The Wild (lien direct) | Recently, Google researchers discovered a local privilege escalation vulnerability in Windows which was being used in zero-day attacks, including those carried out by the Pawn Storm espionage group. This is an easily exploitable vulnerability which can be found in all supported versions of Windows, from Windows 7 to Windows 10. By changing one bit, the attacker can elevate the privileges of a thread, giving administrator access to a process that would not have it under normal circumstances. Post from: Trendlabs Security Intelligence Blog - by Trend Micro One Bit To Rule A System: Analyzing CVE-2016-7255 Exploit In The Wild | APT 28 | |||
| 2016-11-27 19:24:01 | Scapy vs. CozyDuke, (Sun, Nov 27th) (lien direct) | In continuation of observations from my GIAC Security Expert re-certification process, Ill focus here on a GCIA-centric topic: Scapy. Scapy is essential to the packet analyst skill set on so many levels. For your convenience, the Packetrix VM comes preconfigured with Scapy and Snort, so youre ready to go out of the gate if youd like to follow along for a quick introduction. Scapy is a powerful interactive packet manipulation program. It is able to forge or decode packets of a wide number of protocols, send them on the wire, capture them, match requests and replies, and much more. This includes the ability to handle most tasks such as scanning, tracerouting, probing, unit tests, attacks or network discovery, thus replacing functionality expected from hping, 85% of nmap, arpspoof, tcpdump, and others. If youd really like to dig in, grab TJ OConnors Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers (you should already have it), as first discussed here in January 2013. TJ loves him some Scapy: Detecting and Responding to Data Link Layer Attacks is another reference. :-) You can also familiarize yourself with Scapys syntax in short order with the SANS Scapy Cheat Sheet as well. Judy Novaks SANS GIAC Certified Intrusion Analyst Day 5 content offers a nice set of walk-throughs using Scapy, and given that it is copyrighted and private material, I wont share them here, but will follow a similar path so you have something to play along with at home. Well use a real-world APT scenario given recent and unprecedented Russian meddling in American politics. According to SC Magazine, Russian government hackers apparently broke into the Democratic National Committee (DNC) computer systems in infiltrations believed to be the work of two different Russian groups, namely Cozy Bear/ CozyDuke/APT 29 and Fancy Bear/Sofacy/APT 28, working separately. As is often the case, ironically and consistently, one the best overviews of CozyDuke behaviors comes via Kaspersky">syn = IP(src=10.0.2.15, dst=209.200.83.43)/TCP(sport=1337, dport=80, flags=S)/GET /ajax/index.php HTTP/1.1">wrpcap(/tmp/CozyDukeC2GET.pcap, syn), as seen in Figure 2. ">ls(IP). ">Figure 4: ls() If you">|">@holisticinfosec (c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License. | APT 29 APT 28 | |||
| 2016-11-13 19:49:47 | Sednit : dissection d\'un groupe de cyber espions (lien direct) | Les chercheurs ESET annoncent la publication d'un vaste document de recherche en 3 parties " En route... Cet article Sednit : dissection d'un groupe de cyber espions est diffusé par Data Security Breach. | APT 28 | |||
| 2016-11-11 13:44:14 | Pawn Storm used Microsoft zero-day in spear-phishing attacks before patch (lien direct) |  The notorious Pawn Storm group exploited a Microsoft zero-day vulnerability in a number of spear-phishing campaigns before the tech giant had a chance to release a patch.
David Bisson reports. The notorious Pawn Storm group exploited a Microsoft zero-day vulnerability in a number of spear-phishing campaigns before the tech giant had a chance to release a patch.
David Bisson reports.
|
APT 28 | |||
| 2016-11-11 12:30:04 | Sednit: A very digested read (lien direct) | This feature offers a very digested read of ESET's trilogy of research papers on Sednit, one of the most notorious groups of cyberattackers in the world. | APT 28 | |||
| 2016-11-09 19:16:58 | Cyberspies Ramped Up Attacks After Exposure of Zero-Days (lien direct) | The Russia-linked threat actor known as Pawn Storm ramped up its attacks against governments and embassies after seeing that researchers discovered the Windows and Flash Player zero-day exploits it had been using. | APT 28 | |||
| 2016-11-09 17:30:21 | Fancy Bear goes all out to beat Adobe, MSFT zero-day patches (lien direct) | The group behind DNC hack seeks maximum pwnage before patches become widespread. | APT 28 | |||
| 2016-11-09 13:00:34 | Pawn Storm Ramps Up Spear-phishing Before Zero-Days Get Patched (lien direct) | The effectiveness of a zero-day quickly deteriorates as an attack tool after it gets discovered and patched by the affected software vendors. Within the time between the discovery of the vulnerability and the release of the fix, a bad actor might try to get the most out of his previously valuable attack assets. This is exactly what we saw in late October and early November 2016, when the espionage group Pawn Storm (also known as Fancy Bear, APT28, Sofacy, and STRONTIUM) ramped up its spear-phishing campaigns against various governments and embassies around the world.  In these campaigns, Pawn Storm used a previously unknown zero-day in Adobe's Flash (CVE-2016-7855, fixed on October 26, 2016 with an emergency update) in combination with a privilege escalation in Microsoft's Windows Operating System (CVE-2016-7255) that was fixed on November 8, 2016. Post from: Trendlabs Security Intelligence Blog - by Trend Micro Pawn Storm Ramps Up Spear-phishing Before Zero-Days Get Patched | APT 28 | |||
| 2016-11-08 15:59:18 | Microsoft patches 68 vulnerabilities, two actively exploited ones (lien direct) | Microsoft has patched 68 vulnerabilities in Windows, Office, Edge, Internet Explorer and SQL Server, two of which have already been exploited by attackers and three that have been publicly disclosed.The patches are covered in 14 security bulletins, one dedicated to Adobe Flash Player which is upgraded through Windows Update in Windows 10 and 8.1. Six of the bulletins are rated critical and eight are rated important.Administrators should prioritize the Windows patches in the MS16-135 bulletin, because they address a zero-day vulnerability that's already being exploited by a group of attackers known in the security industry as Fancy Bear, APT28 or Strontium.To read this article in full or to leave a comment, please click here | APT 28 | |||
| 2016-11-02 07:51:40 | Windows Zero-Day Exploited by Russia-Linked Cyberspies (lien direct) | The Windows zero-day vulnerability disclosed this week by Google has been exploited by the Russia-linked cyberespionage group known as Strontium. Microsoft has been working on a patch and expects to release it on November 8. | APT 28 | |||
| 2016-11-02 06:41:00 | Microsoft: Windows 0-day exposed by Google is being exploited by Russian DNC hackers (lien direct) | Microsoft issued a warning about the APT group most commonly known as “Fancy Bear,†or APT 28, and how it is exploiting the zero-day disclosed by Google on Halloween.Microsoft agreed that the zero-day is being actively exploited and pointed a finger of blame at a hacking group that is believed to be tied to the Russian government; the same group is believed to be responsible for hacks which resulted in data breaches at the Democratic National Committee and the Clinton campaign.Microsoft does not call the APT group “Fancy Bear†as its codename for the threat group is STRONTIUM. Terry Myerson, executive VP of Microsoft's Windows and Devices Group, wrote:To read this article in full or to leave a comment, please click here | APT 28 | |||
| 2016-11-02 00:50:58 | Windows zero-day exploited by same group behind DNC hack (lien direct) | Microsoft threat teams tied use of bug to APT28, aka "Fancy Bear" | APT 28 | |||
| 2016-11-01 22:44:29 | Microsoft says you\'ll have to wait another week for critical Windows zero-day patch (lien direct) |  The Russian-linked Fancy Bear group (also known as Strontium, APT28, Sednit or Sofacy) have been linked to targeted attacks. The Russian-linked Fancy Bear group (also known as Strontium, APT28, Sednit or Sofacy) have been linked to targeted attacks.
|
APT 28 | |||
| 2016-10-27 03:31:00 | Comment les hackers de Poutine ont espionné le Parti démocrate américain (lien direct) | Des chercheurs en sécurité d'Eset ont décortiqué la trousse à outils du dangereux groupe de pirate APT 28, responsable entre autres du vol de données du parti de Hillary Clinton et du sabotage de TV 5 Monde.  |
APT 28 | |||
| 2016-10-25 12:28:05 | Lifting the lid on Sednit: A closer look at the software it uses (lien direct) | ESET's threat analysts have taken a closer look at the software used by Sednit to spy on its targets and steal confidential information. | APT 28 | |||
| 2016-10-21 13:57:00 | Alien Eye In the Sky 21st October 2016 (lien direct) |
 We’ve got the week’s news covered for you.
In This Week's Episode
Nation State Threat Attribution
Mercedes autonomous cars
Stephen Hawking on AI
Banks failing to report hacks
Indian Bank debit card breach
Other Stories of Interest
Female speakers for your tech event
How hackers handle stolen login data
DFIR and Threat Hunting
The real reason shops want you to sign up for e-receipts
Intelligence Oversight and How It Can Fail
Salesforce’s M&A Target List Excluded Twitter
Poor and/or reused passwords lead to Chinese spam flood on iMessage
Threat report En Route with Sendit
We’ve got the week’s news covered for you.
In This Week's Episode
Nation State Threat Attribution
Mercedes autonomous cars
Stephen Hawking on AI
Banks failing to report hacks
Indian Bank debit card breach
Other Stories of Interest
Female speakers for your tech event
How hackers handle stolen login data
DFIR and Threat Hunting
The real reason shops want you to sign up for e-receipts
Intelligence Oversight and How It Can Fail
Salesforce’s M&A Target List Excluded Twitter
Poor and/or reused passwords lead to Chinese spam flood on iMessage
Threat report En Route with Sendit
|
Guideline | APT 28 | ||
| 2016-10-21 04:43:24 | Comment les hackers de Poutine s\'infiltrent dans nos réseaux (lien direct) | Des chercheurs en sécurité d'Eset ont analysé les outils de l'un des groupes de pirates les plus dangereux de la planète. A savoir APT 28, alias Sofacy ou Fancy Bear.  |
APT 28 | |||
| 2016-10-20 11:30:44 | New ESET research paper puts Sednit under the microscope (lien direct) | Security researchers at ESET have released their latest research into the notorious and highly experienced Sednit cyberespionage group. | APT 28 | |||
| 2016-10-19 11:57:00 | Russian hacker group used phony Google login page to hack Clinton campaign (lien direct) | A Russian hacking group used spearphishing to steal the Gmail login credentials of Hillary Clinton campaign staff, and that may be how campaign emails now being released were stolen, according to Secure Works.The attack targeted 108 hillaryclinton.com email addresses, and was carried out by a Russian group called Threat Group-4127 (TG-4127), according to Secure Works' Counter Threat Unit (CTU) blog.CTU can't directly link the spearphishing operation against the Clinton campaign with the hack of Democratic National Committee emails revealed June 14, but “CTU researchers suspect that TG-4127 used the spearphishing emails or similar techniques to gain an initial foothold in the DNC network. “To read this article in full or to leave a comment, please click here | APT 28 | |||
| 2016-10-06 21:55:23 | Researchers find fake data in Olympic anti-doping, Guccifer 2.0 Clinton dumps (lien direct) | This time, some athlete data was altered by the "Fancy Bear" group. | APT 28 | |||
| 2016-10-06 20:07:44 | Russian Hackers May Have Manipulated Leaked WADA Data (lien direct) | In a statement published Wednesday, October 5, the World Anti-Doping Agency (WADA) provided an update on investigations into the August Fancy Bear hack and data leak in September. FireEye/Mandiant has been employed to do the forensic investigation. As of Oct. | APT 28 | |||
| 2016-09-28 00:01:28 | Aerospace industry warned of targeted attacks from the Komplex OS X trojan (lien direct) |  The Sofacy hacking group (also known as APT28, Sednit, and Fancy Bear) has developed a new trojan called 'Komplex' to help it target OS X users.
David Bisson reports. The Sofacy hacking group (also known as APT28, Sednit, and Fancy Bear) has developed a new trojan called 'Komplex' to help it target OS X users.
David Bisson reports.
|
APT 28 | |||
| 2016-09-27 16:46:42 | Kelly JacksonHiggins: Russian \'Fancy Bear\' group is staying very busy: researchers spot the cyberspies armed with a new Mac OS X Trojan.http://ubm.io/2d6twSUÂ (lien direct) | Kelly JacksonHiggins: Russian 'Fancy Bear' group is staying very busy: researchers spot the cyberspies armed with a new Mac OS X Trojan.http://ubm.io/2d6twSUÂ | APT 28 | |||
| 2016-09-26 23:15:56 | DarkReading: Russian \'Fancy Bear\' Hackers Hit Mac OS X With New Trojanhttp://ubm.io/2duAuiYÂ (lien direct) | DarkReading: Russian 'Fancy Bear' Hackers Hit Mac OS X With New Trojanhttp://ubm.io/2duAuiYÂ | APT 28 | |||
| 2016-09-26 17:00:00 | Russian \'Fancy Bear\' Hackers Hit Mac OS X With New Trojan (lien direct) | Aerospace victim hit by targeted attack that didn't even exploit a Mac vulnerability. | APT 28 | |||
| 2016-09-26 10:00:00 | What The WADA Hack Proves About Today\'s Threat Landscape (lien direct) | Fancy Bear's initial release of data on four top American athletes reminds us all to reassess our risks. | APT 28 | |||
| 2016-09-17 08:20:46 | Alain Charret: Fancy Bears hacking group has ties to Russian presidency, US cyber security experts say... (Radio Australia) (lien direct) | Alain Charret: Fancy Bears hacking group has ties to Russian presidency, US cyber security experts say... (Radio Australia) | APT 28 | |||
| 2016-09-16 07:03:21 | Hackers Leak More Confidential Athlete Data (lien direct) | The hacker group calling itself Fancy Bears has leaked another batch of athlete medical records stolen from the systems of the World Anti-Doping Agency (WADA). The organization has confirmed the leak and again blamed Russia for the attack on its systems. | APT 28 |
To see everything:
Our RSS (filtrered)
